myCSUSM
myCSUSMInformation Security Awareness April 2018
Multifactor Authentication (MFA)
Multifactor Authentication is coming! This year the campus is beginning to roll out multifactor authentication. You are probably already using MFA with your bank, or other website or mobile app. MFA is sometimes called two-factor or 2-step verification. It means that when you log in, you may be required to use an additional step such as entering a code delivered to your mobile phone.
Starting with a small pilot group, over the next six months, we will begin rolling out MFA to employees based on the applications they access. Starting with the Common Financial System late this spring, we will enroll staff who access CFS with “Duo”, a multi-factor authentication system purchased by the CSU. Enrollment is simple and easy. Once enrolled, employees who access CFS will need to enter both their campus password and, if logging in with an untrusted device or browser, enter the code that is sent to their phone.
To see an demonstration of MFA, click below:
Look for more info about MFA @ CSUSM coming soon!

Facebook? Cambridge Analytica? What’s going on?
You may have heard the saying, “If you’re not paying for the product, you are the product”. For those of us in the cybersecurity industry, the news of the Fakebook Cambridge Analytica scandal came of no surprise. If fact, this public revelation should be less about Facebook and more about the much larger problem of data brokering.
Let’s start with the Cambridge Analytica scandal. According to Zuckerberg himself, “In 2013, a Cambridge University researcher named Aleksandr Kogan created a personality quiz app. It was installed by around 300,000 people who shared their data as well as some of their friends' data. Given the way our platform worked at the time this meant Kogan was able to access tens of millions of their friends' data.” Kogan sold this data to Cambridge Analytica, a political consulting firm. The Channel 4 News, a British news program, discovered that the company uses mined data to personalize political messages with the goal of influencing elections. They appear to sell this as a service. Allegedly, their services were used during the 2016 presidential election.
This story begins to shed light on the problem of data brokering, a multi-billion-dollar industry made up of companies who collect consumer data and sell it to other companies, usually for marketing purposes. There are over four thousand data broker companies worldwide and as of now, it is totally legal. Places like storefronts collect info from your loyalty cards to sell to advertisers. The three big credit bureaus make money by selling your information to banks, credit card companies and any financial institution that would lend consumers money. Many large companies such as Facebook and Google sell your data, from from your web browsing habits to your sexual orientation. These third party companies create dossiers on individuals, and sell this information. Data brokering is notoriously secretive, with many companies sharing little how this data is used.
What can you do? This is a tough problem. There are a few steps you can take now. Clear your cookies. Limit personal data on social media. Employ privacy tools like a VPN or the DuckDuckGo search engine. You can browse with the Tor browser for added privacy. Skip store loyalty cards. Limit ad tracking on your smartphone in privacy settings. Log out of social media sites while using the web. This situation will only be addressed by consumer outcry.
New Phishing Methods
Throughout the first few months of 2018, we have seen an increase in the number of phishing attempts on our campus. (Phishing is a type of social engineering attack perpetrated by individuals that want to steal your credentials.)
Often, attackers want to steal your credentials so that they can send more phishing emails. This means that the more people that falling for phishing schemes means more phishing schemes will be attempted, and these are the often the most dangerous types of phishing attacks because they can come from legitimate campus email accounts. In other cases, attackers use phishing methods for identity theft, financial fraud and delivery of malware to your computer.
Just because it looks like it came from someone you know (or someone in your organization, doesn’t mean that it actually came from that person (you can forge the “From” address!); or maybe it really did come from said person, but that doesn’t mean it’s not malicious. Evaluate the content of the message, not just the sender! Hover your cursor over any links that the message contains to see if the URL will send you to an unexpected website. Don't download an open that attachment!
For more phishing tips, check out these resources:
- Somethings Phishy: How to detect phishing attempts
- 10 tips on how to identify a phishing or spoofing email
- 10 tips for spotting a phishing email
- 5 ways to spot a phishing email
Spoofing
Spoofing is a technique used by attackers to trick people. It is often used in conjunction with a phishing attempt. It is easy to spoof a web page, email address, IP address, and even phone number!
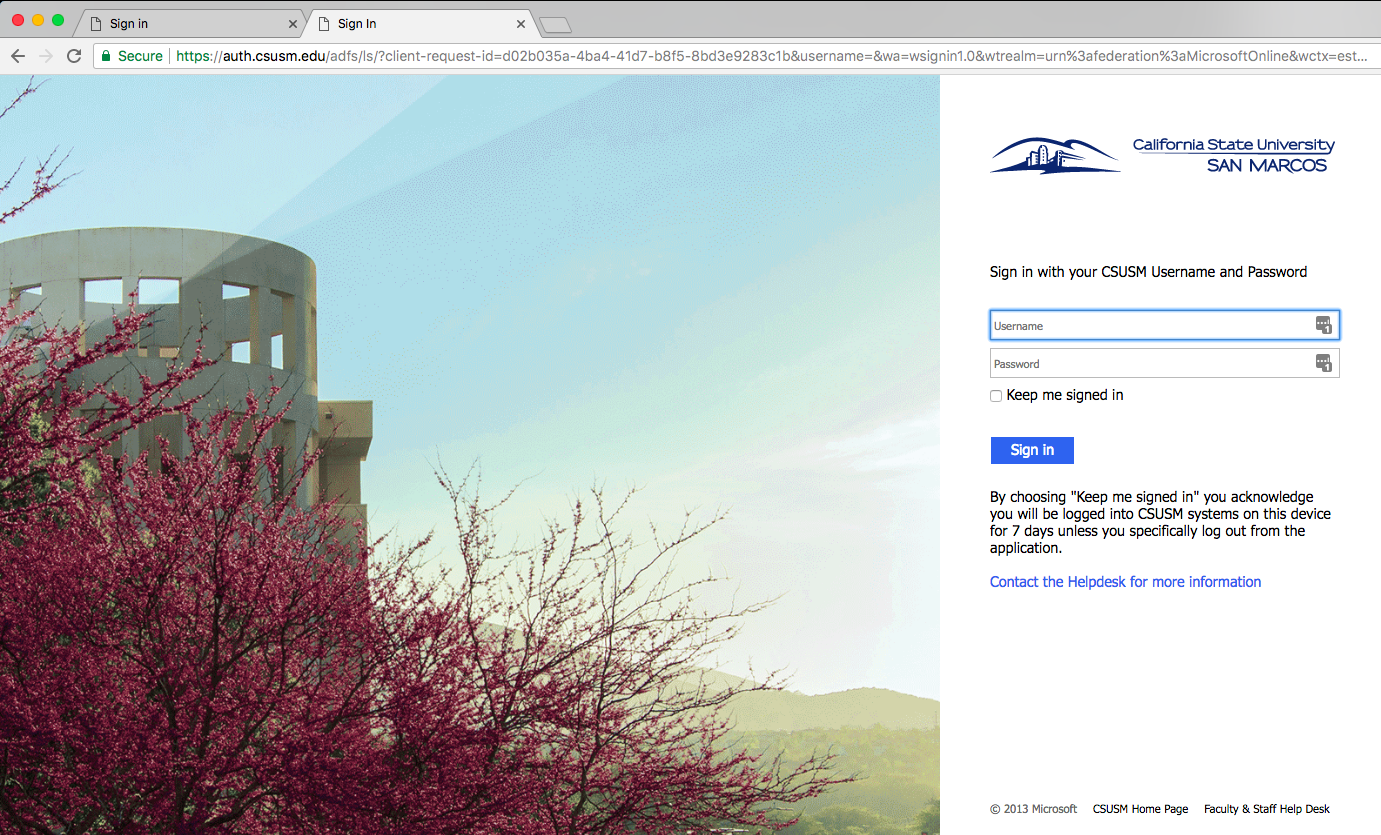
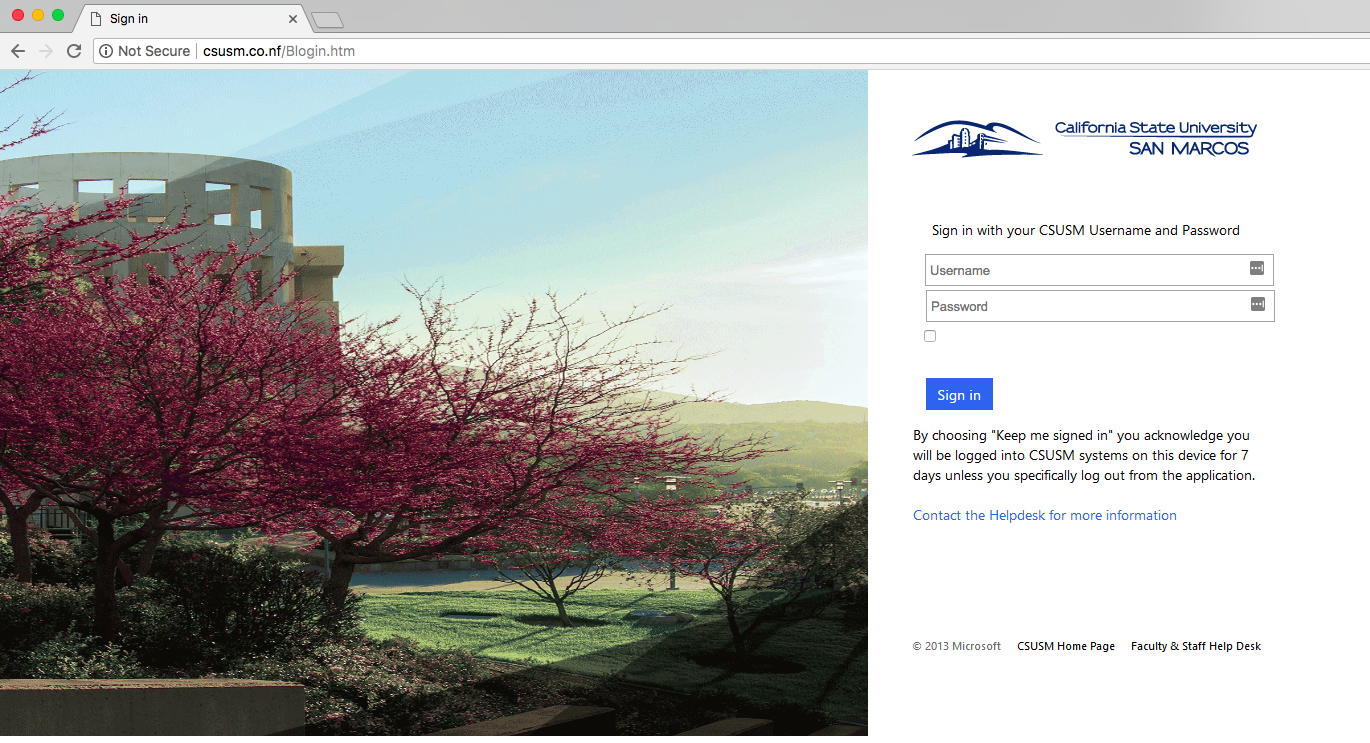
One of the most common forms of spoofing is web page spoofing. Attackers often create fake web pages that look like real sign-on pages to capture the credentials of unsuspecting users. Attackers then use those credentials to send out more phishing attempts. It is a vicious cycle!
Look at the images below. Can you tell which one is forged?